Microsoft Windows was, to some people, too little, too late.
Released as Version 1.0 in 1985, the graphic revolution was already happening elsewhere, with other computer operating systems – but Microsoft was determined to catch up, no matter what it cost or took. Version 1.0 of their new multi-tasking navigation program (it was not quite an “Operating System”) appeared and immediately got marks for being a step in the right direction, but not quite a leap. Later versions, including versions 2.0 and 2.1, finished out the late 1980s with a set of graphics-oriented programs that could be run from DOS and allow the use of a mouse/keyboard combination (still new at the time) and a chance for Microsoft to be one of the dominant players in graphical interfaces. It also got them a lawsuit from Apple, which ultimately resulted in a many-years court case and a settlement in 1997 that possibly saved Apple.
Meanwhile, the Windows shell started to become more an more like an operating system, and the introduction of Windows 3.0 and 3.1 brought stability, flexibility, and ease-of-programming to a very wide audience, and cemented the still-dominant desktop paradigms in use today.
In 2015, the Internet Archive started the year with the arrival of the DOS Collection, where thousands of games, applications and utilities for DOS became playable in the browser with a single click. The result has been many hundreds of thousands of visitors to the programs, and many hours of research and entertainment.
This year, it’s time to upgrade to Windows.
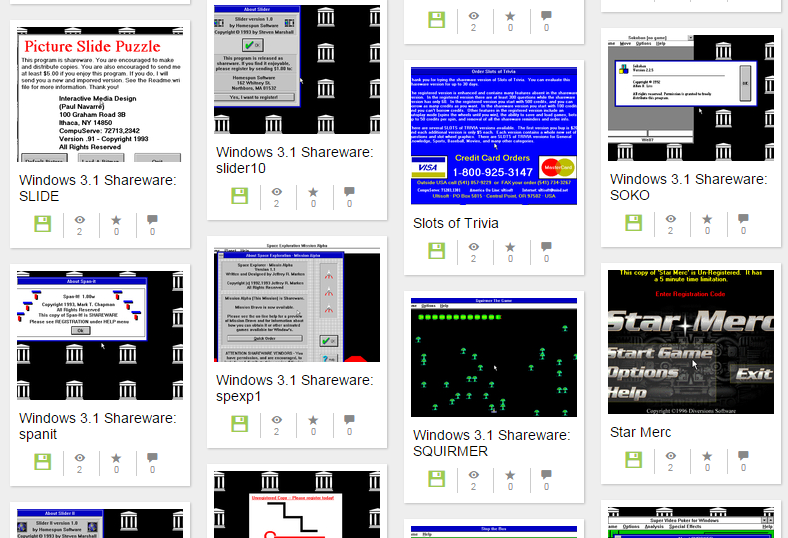
We’ve now added over 1,000 programs that run, in your browser, in a Windows 3.1 environment. This includes many games, lots of utilities and business software, and what would best be called “Apps” of the 1990s – programs that did something simple, like provide a calculator or a looping animation, that could be done by an individual or small company to great success.
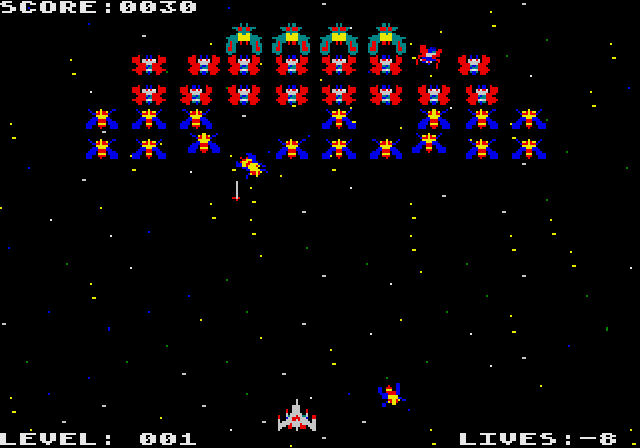
Indeed, the colorful and unique look of Windows 3/3.1 is a 16-bit window into what programs used to be like, and depending on the graphical whims of the programmers, could look futuristic or incredibly basic. For many who might remember working in that environment, the view of the screenshots of some of the hosted programs will bring back long-forgotten memories. And clicking on these screenshots will make them come alive in your browser.


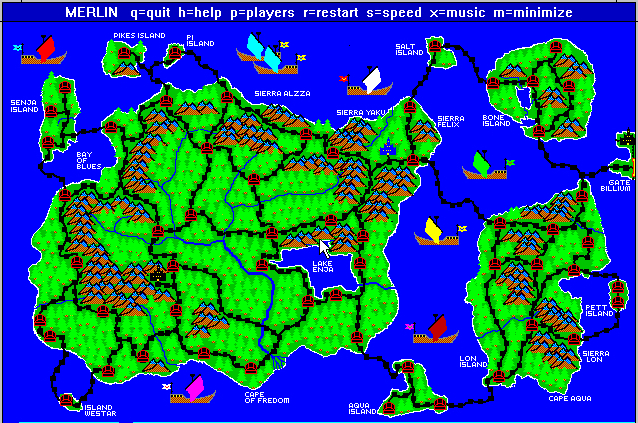
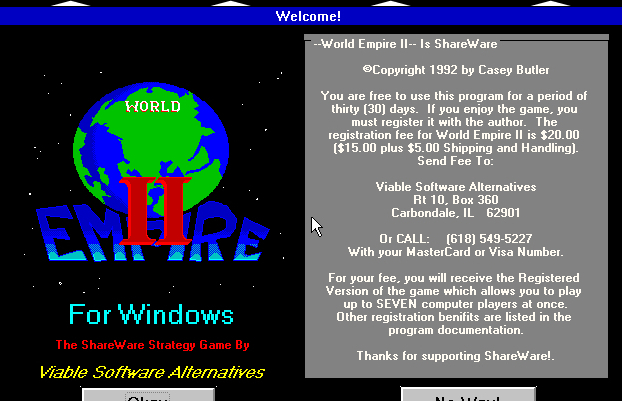 When they focused on it, a developer could produce something truly unique and beautiful within the Windows 3.x environment. Observe this Role-Playing Game “Merlin”:
When they focused on it, a developer could produce something truly unique and beautiful within the Windows 3.x environment. Observe this Role-Playing Game “Merlin”:
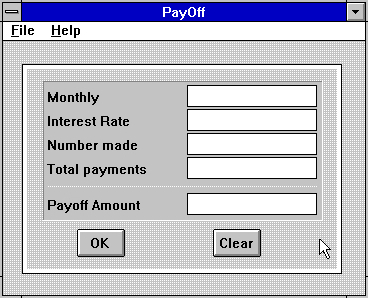
But on the whole, the simple libraries for generating clickable boxes and rendering fonts, and an intent to “get the job done” meant that a lot of the programs would look like this instead:
(Then again, how complicated and arty does a program to calculate amortization amounts have to be?)
Windows 3.1 continues to be in use in a few corners of the world – those easily-written buttons-and-boxes programs drive companies, restaurants, and individual businesses with a dogged determination and extremely low hardware requirements (a recent news story revealed at least one French airport that depended on one).
Many people, though, moved on to Microsoft’s later operating systems, like Windows 95, ME, Vista, 7, and so on. Microsoft itself stopped officially supporting Windows 3.1 in 2001, 15 years ago.
But Windows 3.1 still holds a special place in computer history, and we’re pleased to give you a bridge back to this lost trove of software.
If you need a place to start without being overwhelmed, come visit the Windows Showcase, where we have curated out a sample set of particularly interesting software programs from 20 years ago.
As is often the case with projects like this, volunteers contributed significant time to help bring this new library of software online. Justin Kerk did the critical scripting and engineering work to require only 2 megabytes to run the programs, as well as ensure that the maximum number of Windows 3.1 applications work in the browser-based emulator. (Justin thanks Eric Phelps, who in 1994 wrote the SETINI.EXE configuration program). db48x did loader programming to ensure we could save lots of space. James Baicoianu did critical metadata and technical support. As always, the emulation for Windows and DOS-based programs comes via EM-DOSBOX, which is a project by Boris Gjenero to port DOSBOX into Javascript; his optimization work has been world-class. And, of course, a huge thanks to the many contributing parties of the original DOSBOX project.